1 Overview
To generate a self-signed cert with longer expiration date, like 5-10 years from now, a custom script which utilizes some built-in COM component is needed. We utilize the built-in COM components to provide platform independence, as different versions of Windows Server support different options in the original PowerShell command to create a self-signed cert.
Note: This cert cannot be used to implement https on a public web site. Its main intention is to allow sign and validation in Azure Application auth between DynamicPoint Office 365 products and Azure.
2 Script
The PowerShell script for creating the self-signed cert can be downloaded from here.
Instructions
- To run the script, you need to provide two parameters:
– certSubject – specify a string which will be used as a subject and name for the cert, for instance “DynamicPoint Inc.”
– certExpInYears – number of years from current date in which the cert will be valid, for instance 14 - Once you run the script, if no errors occur, you can find the cert in Manage computer certificates console:
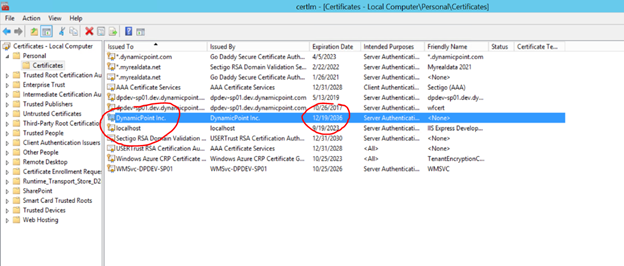
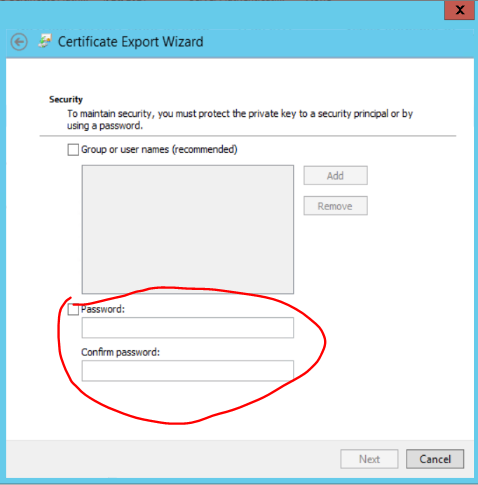
- To export the certificate in .pfx and .cer formats, you need to right click on the cert , All Tasks, Export, and chose the needed format and settings.
- When exporting as .pfx (includes the private key), please add password to provide better security.
Copy of the Script
param([string]$certSubject, [int]$certExpInYears)
$name = new-object -com “X509Enrollment.CX500DistinguishedName.1”
$name.Encode(“CN=” + $certSubject, 0)
$key = new-object -com “X509Enrollment.CX509PrivateKey.1”
$key.ProviderName = “Microsoft RSA SChannel Cryptographic Provider”
$key.KeySpec = 1
$key.Length = 2048
$key.SecurityDescriptor = “D:PAI(A;;0xd01f01ff;;;SY)(A;;0xd01f01ff;;;BA)(A;;0x80120089;;;NS)”
$key.MachineContext = 1
$key.ExportPolicy = 1
$key.Create()
$serverauthoid = new-object -com “X509Enrollment.CObjectId.1”
$serverauthoid.InitializeFromValue(“1.3.6.1.5.5.7.3.1”)
$ekuoids = new-object -com “X509Enrollment.CObjectIds.1”
$ekuoids.add($serverauthoid)
$ekuext = new-object -com “X509Enrollment.CX509ExtensionEnhancedKeyUsage.1”
$ekuext.InitializeEncode($ekuoids)
$cert = new-object -com “X509Enrollment.CX509CertificateRequestCertificate.1”
$cert.InitializeFromPrivateKey(2, $key, “”)
$cert.Subject = $name
$cert.Issuer = $cert.Subject
$cert.NotBefore = get-date
$cert.NotAfter = $cert.NotBefore.AddYears($certExpInYears)
$cert.X509Extensions.Add($ekuext)
$cert.Encode()
$enrollment = new-object -com “X509Enrollment.CX509Enrollment.1”
$enrollment.InitializeFromRequest($cert)
$certdata = $enrollment.CreateRequest(0)
$enrollment.InstallResponse(2, $certdata, 0, “”)
